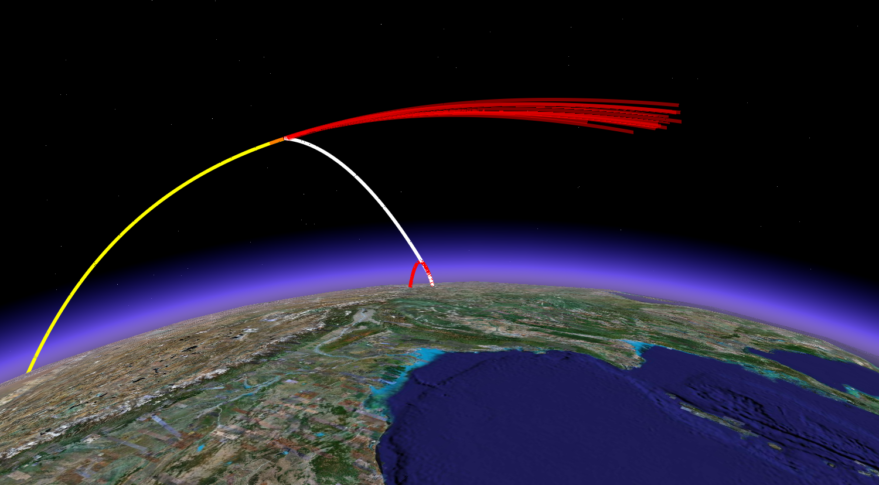
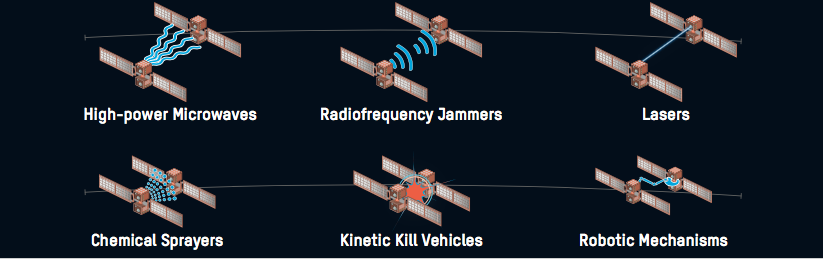
Cyber Hegelianism
Capt Wardrobe Dec 2020 - June 2021
Problem; The hacking of infrastructure
National defense compromised?
|
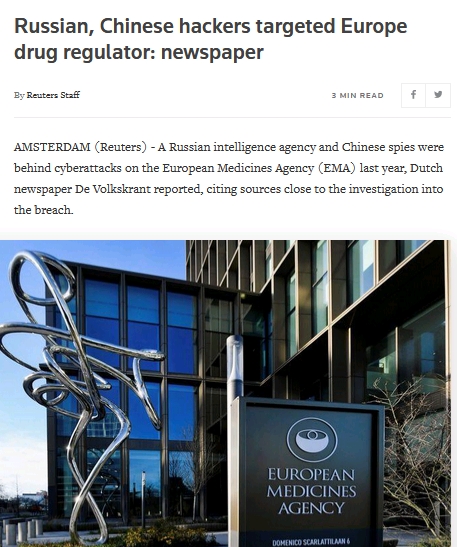
Malicious Domain in SolarWinds Hack Turned into 'Killswitch'
A key malicious domain name used to control potentially thousands of computer systems compromised via the months-long breach at network monitoring software vendor SolarWinds was commandeered by security experts and used as a "killswitch" designed to turn the sprawling cybercrime operation against itself, KrebsOnSecurity has learned.
Austin, Texas-based SolarWinds disclosed this week that a compromise of its software update servers earlier this year may have resulted in malicious code being pushed to nearly 18,000 customers of its Orion platform. Many U.S. federal agencies and Fortune 500 firms use(d) Orion to monitor the health of their IT networks.
On Dec. 13, cyber incident response firm FireEye published a detailed writeup on the malware infrastructure used in the SolarWinds compromise, presenting evidence that the Orion software was first compromised back in March 2020. FireEye said hacked networks were seen communicating with a malicious domain name - avsvmcloud[.]com - one of several domains the attackers had set up to control affected systems.
As first reported here on Tuesday, there were signs over the past few days that control over the domain had been transferred to Microsoft. Asked about the changeover, Microsoft referred questions to FireEye and to GoDaddy, the current domain name registrar for the malicious site.
Today, FireEye responded that the domain seizure was part of a collaborative effort to prevent networks that may have been affected by the compromised SolarWinds software update from communicating with the attackers. What's more, the company said the domain was reconfigured to act as a "killswitch" that would prevent the malware from continuing to operate in some circumstances.
"SUNBURST is the malware that was distributed through SolarWinds software," FireEye said in a statement shared with KrebsOnSecurity. "As part of FireEye's analysis of SUNBURST, we identified a killswitch that would prevent SUNBURST from continuing to operate."
The statement continues:
"Depending on the IP address returned when the malware resolves avsvmcloud[.]com, under certain conditions, the malware would terminate itself and prevent further execution. FireEye collaborated with GoDaddy and Microsoft to deactivate SUNBURST infections."
"This killswitch will affect new and previous SUNBURST infections by disabling SUNBURST deployments that are still beaconing to avsvmcloud[.]com. However, in the intrusions FireEye has seen, this actor moved quickly to establish additional persistent mechanisms to access to victim networks beyond the SUNBURST backdoor.
This killswitch will not remove the actor from victim networks where they have established other backdoors. However, it will make it more difficult to for the actor to leverage the previously distributed versions of SUNBURST."
It is likely that given their visibility into and control over the malicious domain, Microsoft, FireEye, GoDaddy and others now have a decent idea which companies may still be struggling with SUNBURST infections.
The killswitch revelations came as security researchers said they'd made progress in decoding SUNBURST's obfuscated communications methods. Chinese cybersecurity firm RedDrip Team published their findings on Github, saying its decoder tool had identified nearly a hundred suspected victims of the SolarWinds/Orion breach, including universities, governments and high tech companies.
Meanwhile, the potential legal fallout for SolarWinds in the wake of this breach continues to worsen. The Washington Post reported Tuesday that top investors in SolarWinds sold millions of dollars in stock in the days before the intrusion was revealed. SolarWinds's stock price has fallen more than 20 percent in the past few days. The Post cited former enforcement officials at the U.S. Securities and Exchange Commission (SEC) saying the sales were likely to prompt an insider trading investigation.
source Krebson Security
|
Mike Pompeo; Russia responsible for the attack
|
|
December 20, 2020 -
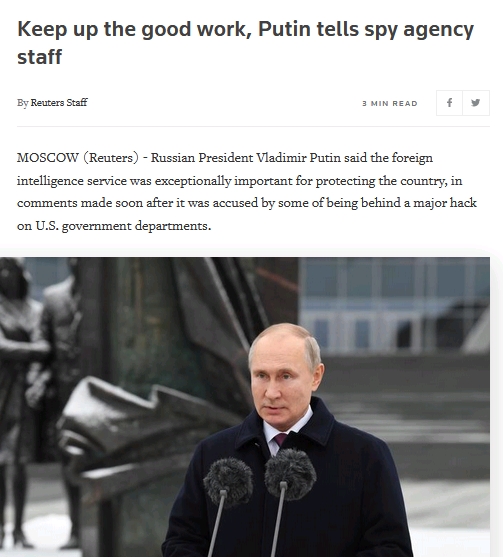
MOSCOW (Reuters) - Russian President Vladimir Putin said the foreign intelligence service was exceptionally important for protecting the country, in comments made soon after it was accused by some of being behind a major hack on U.S. government departments.
Speaking at an event commemorating 100 years since the founding of the SVR foreign intelligence service, Putin said the agency and other security services were a crucial guarantee of Russia's "sovereign, democratic, independent development."
Some international cyber researchers have suggested that Russia's SVR foreign intelligence service may have been behind an unprecedented attack on U.S. government computer systems first reported by Reuters last week.
U.S. Secretary of State Mike Pompeo said on Friday that Russia was responsible for the attack. The Kremlin has always denied Moscow's involvement in cyber attacks against the West. It has said that Russia had nothing to do with this latest assault.
Putin told attendees of the event, which also marked the Day of the Security Services Worker, that it was important to continue developing the work of counterintelligence agencies.
"I know what I'm talking about here," Putin, a former KGB agent, said, in comments shared on the Kremlin website. "And I rate very highly the difficult professional operations that have been conducted."
"The most serious attention must be paid to information security, to the fight against extremism and against corruption," he added.
He also told members of the agency to pay particular attention to risks posed by conflicts "simmering" near the country's borders.
Clashes have again been reported between Armenia and Azerbaijan over the Nagorno-Karabakh enclave despite a Russian-brokered ceasefire. Weekly anti-government protests continue in Belarus.
"I expect that the Foreign Intelligence Service will continue to respond flexibly to the highly changeable international context, actively participating in identifying and neutralising potential threats to Russia, and improving the quality of its analytical materials," Putin said.
Reuters
|
|
|
The Biden administration is moving to treat ransomware attacks as a national security threat, using intelligence agencies to spy on foreign criminals and contemplating offensive cyber operations against hackers inside Russia, U.S. officials and other sources familiar with the matter tell NBC News.
Though using the military to take action against criminals would not be without precedent, it's controversial in legal circles, and any American cyber action against targets in Russia would risk retaliation. But officials say criminal ransomware attacks from abroad, once a nuisance, have become a major source of economic damage, as the disruption of gasoline and meat supplies in recent weeks has illustrated.
"Right now, they are hair on fire," one former government official said of the Biden administration.
In an example of the new approach, the White House was unusually quick to point the finger at Russia for harboring the attackers, just one day after officials learned of the ransomware strike on meat processor JBS. In previous incidents, it took weeks or months for the U.S. government to publicly blame another country as the source of a cyber attack.
|
|
But momentum was building even before Biden took office. As the onslaught of ransomware attacks against hospitals and local governments increased, the National Security Agency in the summer of 2019 began spying on certain foreign criminal hacker groups, according to a former official and three other sources familiar with the matter. Officials say that intelligence collection puts the U.S. in a better position to target the groups if the president orders a strike.
Because they are not carried out directly by governments, ransomware attacks like the ones that hit Colonial Pipeline and JBS have for years been treated as purely criminal matters, investigated by the FBI with an eye toward prosecution. Criminal accountability was rare, though, because most of the hackers reside in Russia and other places outside the reach of American law enforcement. Russia allows the hackers to operate without interference as long as they are attacking the West, U.S. officials say.
Even as the NSA began assembling data on ransomware groups, hospital systems were hit last fall by another wave of attacks. Sources say U.S. officials in charge of cyber policy became further convinced that it was time to get more intelligence resources — and military cyber warriors — focused on the problem.
"Sometime at the end of last year, everyone decided that this had risen to the level of a threat to national security," said James Lewis, a cyber expert at the Center for Strategic and International Studies who consults frequently with government officials.
|
|
|
|
Spokespersons for the NSA and U.S. Cyber Command declined to comment.
"While we won't comment on specific planned or ongoing operations, we provide options through the Department of Defense to the president," the cyber command spokesperson said.
Since Biden took office, the impact of ransomware attacks has grown, officials say. An attack on Colonial Pipeline last month led to gasoline shortages, and a strike against meat processing firm JBS threatened a quarter of America's meat processing capacity. Had JBS not gotten back online quickly —presumably by paying a ransom — experts say Americans might have experienced significant meat shortages.
On Thursday, Anne Neuberger, Deputy National Security Advisor for Cyber and Emerging Technology, issued an open letter to corporate leaders urging them to improve their cyber defenses.
"The number and size of ransomware incidents have increased significantly," she said. "The U.S. government is working with countries around the world to hold ransomware actors and the countries who harbor them accountable, but we cannot fight the threat posed by ransomware alone. The private sector has a distinct and key responsibility."
Neuberger also said the U.S. government was seeking to "disrupt" ransomware networks, though she didn't say how.
|
|
In a typical ransomware attack, hackers break into a corporate network and lock up data, demanding payment in order to release it. Some also threaten to post business secrets on the internet if payment is not made.
Cyber security experts say successful ransomware attacks often take advantage of companies with substandard cyber defenses.
But even if every company and local government had the best defensive technology in place, hackers with enough time and money would find a way to get through, experts say. That's why the Biden administration is contemplating ways to deter ransomware gangs and the countries that give them sanctuary, principally Russia.
The White House says Biden will put Russian President Vladimir Putin on notice at the June 16 summit between the two leaders that Russia must stop harboring criminal hackers. But Lewis and other experts do not anticipate Putin caving to U.S. demands.
If he doesn't, Biden will have a menu of options in front of him, current and former officials say, including offensive action by U.S. Cyber Command, the military hackers based at Fort Meade who wield cyber weapons that can take down networks and turn computers into bricks.
The military would be careful to operate in a gray area, just short of the international law definition of an act of war, said Gary Brown, a former Pentagon cyber warrior who now serves as professor of cyber law at the National Defense University. That's exactly what Russia has been doing to the U.S. over the last decade, he said, with a campaign of disinformation, election interference and hacking.
|
|
|
|
Among the things Cyber Command could do, he said, is disrupt the hackers' ability to access their own networks and tools, "infect their networks with modified tools that have our own little special gifts attached to them," and harass some of the key players.
Indictments by the Justice Department also serve a purpose, he said, by blocking the hackers from most travel and access to the U.S. financial system.
The U.S. could also impose further economic sanctions on Russia, but "we've kind of pressed the sanctions button pretty close to the max," Brown said. "In my opinion, we seem to have kind of run the course on how much you can do with that."
Whatever the U.S. response has been, it hasn't led Russia to stop harboring the criminal hackers, said Glenn Gerstell, who retired in 2020 after five years as NSA general counsel.
"We're not going to shut off all the lights in Moscow," he said, but "whatever it is we're doing now is clearly not producing the desired effect. We need to do something different."
Some scholars have urged caution in the use of the military against criminal hackers. Jason Healy, a former White House official who is now a cyber expert at Columbia University, made that argument in an article for the Lawfare blog last month, saying the military should only be used against criminal groups as a last resort, in response to an imminent threat.
|
|
Military force has been used against criminals before, in raids to free American hostages, such as when Navy SEALs rescued merchant ship crew members from Somali pirates in 2009, an incident later portrayed in the Tom Hanks movie, "Captain Phillips."
And in August 2020, current and former officials say, U.S. Cyber Command took down a Trickbot, a botnet used to deploy ransomware. That was the first known use of military force against criminal hackers, and it was justified as a measure to prevent election interference, because Trickbot also could have been repurposed to disrupt the 2020 elections.
Cyber command's mission is to defend the United States in cyberspace, Gerstell said.
"If the country is experiencing malicious effects from a cyber attack, that to me creates a justification for U.S. Cyber Com to be more aggressive," he said.
Source - CNBC
|
|
How did the FBI recover the ransomeware money? how did they infiltrate the operations of "The Darksides" Crypto Blockchain activity - some interesting revelations here
|
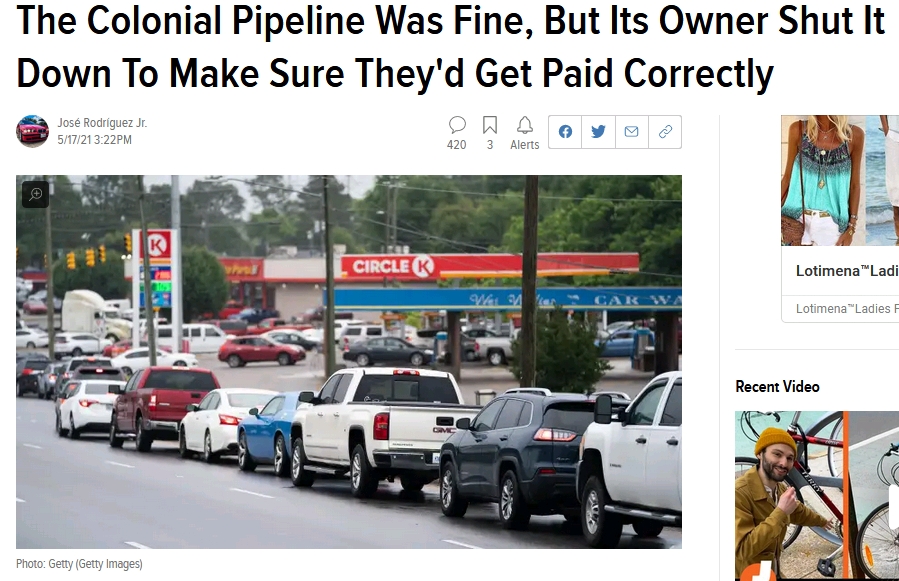
Colonial pipeline Attack... a PSYOP?
|
|
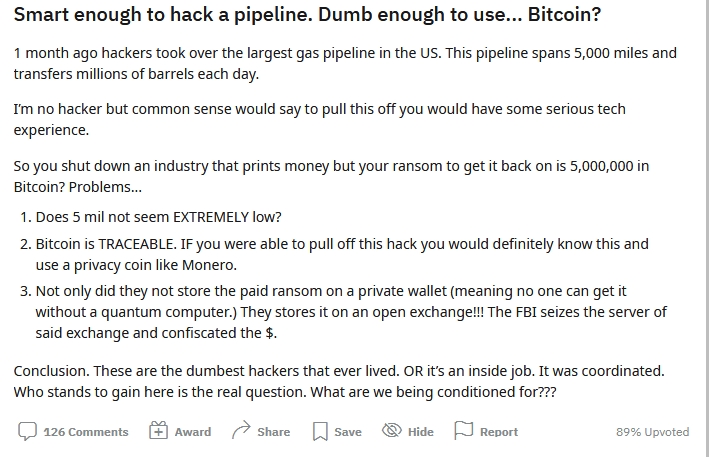
Did the FBI just recover the Colonial Pipeline ransom money from itself? The narrative of a sophisticated hacking group seems to be falling apart.
Posted on June 9, 2021 - Tyler S. Farley
The FBI was looking to send a big message yesterday to would-be criminals when they announced they had recovered the Bitcoin ransom paid to the supposed hacking group which shut down the Colonial Pipeline with a ransomware attack last month.
But less than 24 hours later, their message seems to be getting a little cloudy and instead is drawing scrutiny as to what actually happened.
At first, the FBI reported the news of them recovering the Bitcoin as some act of sophisticated digital forensics that was an example of the far reach of the FBI. However, it turns out the Bitcoin was sitting comfortably and easily accessible on a custodial account in northern California.
Yes, California. Despite the mainstream news once again parroting "muh Russia" as soon as the ransomware attack went public, it turns out the ransom was sent to an exchange or other type of custodial Bitcoin address in California.
|
|
What's even more puzzling than the location is the fact that the so-called sophisticated hacking group didn't even realize that Bitcoin held in a custodial type exchange is not really owned by them. This fact is well known to even amateur Bitcoin users and investors who almost always use personal wallets they control, not custodial accounts on exchanges to hold their Bitcoins. Yet somehow, these hackers which were able to bring down entire critical infrastructures were unaware of that fact.
Once the FBI learned where the Bitcoin was being stored using basic publicly available tools, they simply applied for a court order to seize it, which they did with a simple phone call.
So as of now, the "conclusion" of this story seems to really be just the beginning of realizing the whole thing is not what it was reported to be in the first place.
From the beginning we were told the hack was done by a foreign group with very sophisticated techniques and methods. Yet now we see they were total amateurs who couldn't even properly store the Bitcoin ransom they asked for. By the way, personal Bitcoin wallets are free to download and use by anyone. So if the hackers simply downloaded a free wallet, they would still have their millions of dollars. It all just doesn't make sense.
What's worse is the FBI is clearly hoping the public is too stupid to realize their story is completely bogus. But considering tens of millions of people own and invest in Bitcoin, I doubt that will be the case.
Right about now some people would argue that criminals are often stupid and do stupid things, but that applies to strong-arm criminals who rob liqueur stores and steal purses. Hackers are a totally different breed of criminals and are usually some of the most intelligent people in the world, especially within their realm of computers. Bitcoin storage should fall right into their wheelhouse of expertise, yet the FBI is now essentially telling us these hackers had no idea what they were doing.
So as I mentioned earlier, it seems like this story is just starting instead of being wrapped up. The narrative of a sophisticated hacking group being responsible is now falling apart and no new explanation has been offered. Many people with knowledge of hacking and Bitcoin are starting to wonder if this was some sort of false flag because they can't believe any hacker would be so stupid as to not store their Bitcoin in a personal wallet.
The Culture Chronicles
|
|
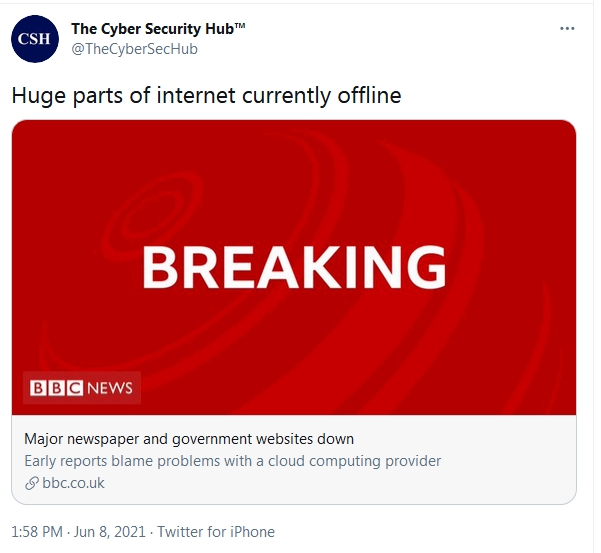
ARE OTHER PARTS OF THE INTERNET SIMILARLY VULNERABLE?
Like the content distribution network world, cloud computing—when computing services are entrusted to a remote provider—is dominated by just a few major players led by Amazon Web Services, Google and Microsoft. Amazon, the biggest cloud provider, periodically has brief outages, which are a big deal for customers.
"And if it became a major outage of, say, more than six, eight hours—but days—it could put companies out of business," said Josh Cheesman, an analyst with the tech market researcher Gartner Inc.
The question is: What could cause such a serious outage that might destroy customer data? A major cyberattack is one possibility. Another is fire or catastrophic natural disaster. These businesses, after all, are based in datacenters. In March, a fire at a datacenter in Strasbourg, France, owned by a major cloud computing firm knocked out service to millions of websites.
[my italics]
SHOULD THE GOVERNMENT REGULATE THESE FIRMS? WHAT CAN COMPANIES AND INDIVIDUALS DO TO PROTECT THEMSELVES?
TechXplore via PHys.org
|
|
|
The Empire fights back!
Solution: ownership of all digital realms...
via Top down space based
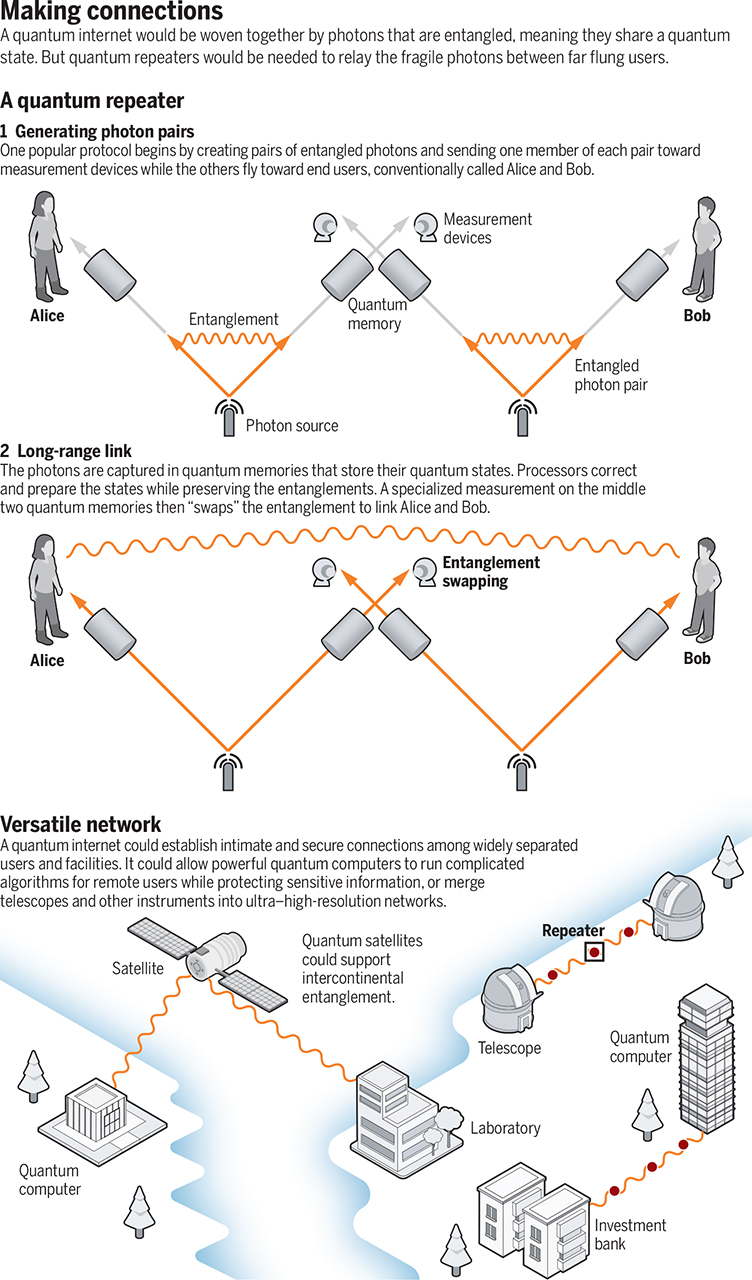
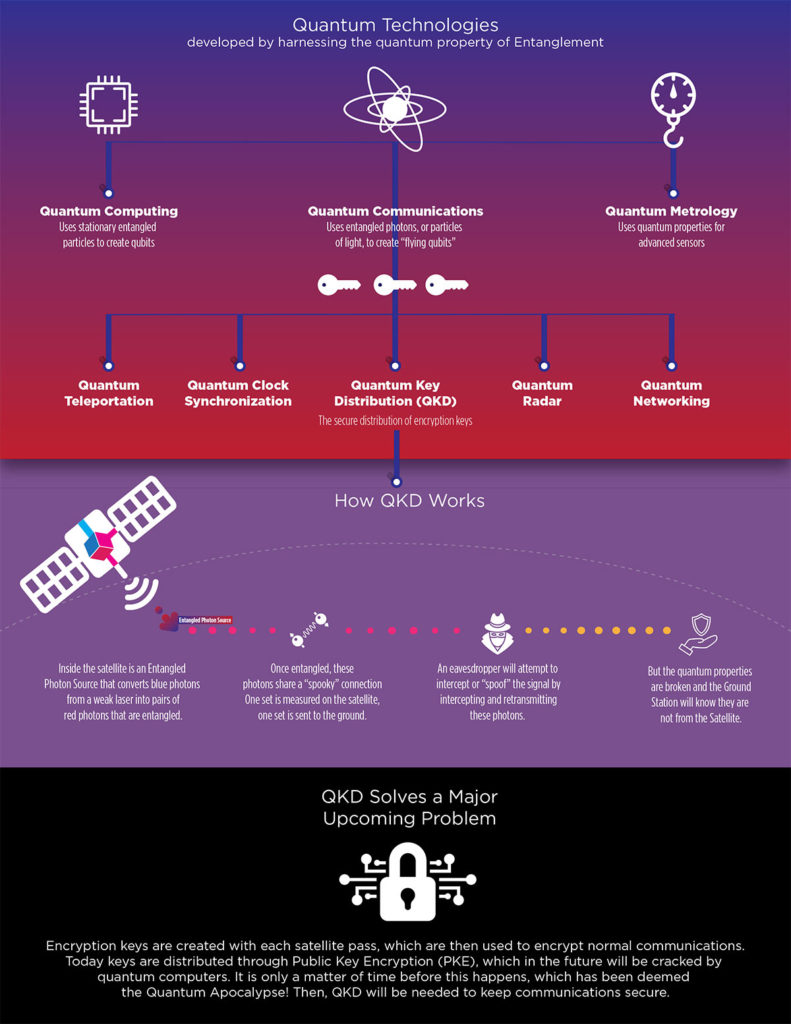
unhackable Quantum based cyber systems
enabling criminalizing decentralized Blockchain / Crypto...
and enabling measures such as introducing CBDC
...and a social credit system...
Globally
|
|
CBDCs being taken seriously
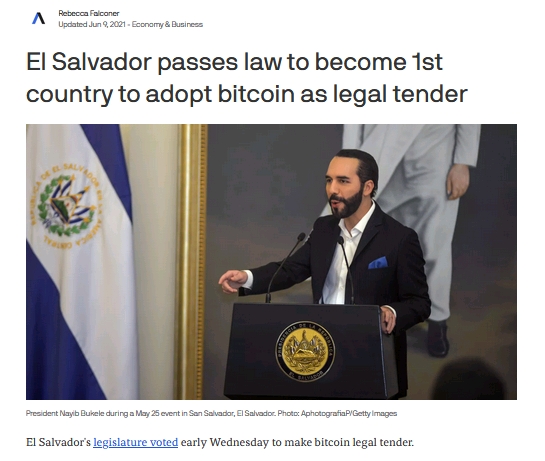
Crypto adopted as currency in El salvador
Iran? France & Switzerland?
|
Do you want to live in a world where every purchase you make and every interaction you have with others is recorded, documented and unchangeable?
What about a world where everyone is manipulated into rating each other in some kind of evil social rating system on a daily basis?
Your every move is recorded and every website you visit is documented. Every book you read, every time you step off the curb before the light changes, and every time you go even one unit above the speed limit it is used against you. If your score drops, you lose access to travel and quality food, and if it drops enough you eventually lose your home and become untouchable with no hope of ever getting ahead in life.
Asia Times
|
According to a report from state-run media, "Remin Chain," from Hangzhou's Hyperchain Technology, will be integrated into the People's Daily Online Public Opinion Monitoring Center—the government apparatchik responsible for monitoring and analyzing every comment made online by China's 800 million netizens. As the name implies, the center is run by People's Daily, one of the mouthpieces of the Communist Party.
|

|
follow the money/control of data
The news of Peter Thiel as an investor in Block.One was reiterated with the announcement of Bullish, the upcoming crypto Exchange developed by Block.One and integrated with EOS. Indeed, Peter Thiel was among the investors who led the capital raise for Bullish for about $300 million. In addition Peter Thiel, along with Alan Howard, Richard Li, and Christian Angermayer will serve as senior advisors to the company.
As a result, Thiel's engagement with Block.one is encouraging. This is especially relevant as Palantir went public and PLTR stock was quickly snatched up by traders, making it another large profit for Thiel. Given Palantir's experience in big data, crypto appears to be an obvious next step. - Source
|
|
Elon Musk's SpaceX announced Thursday that Google would team up with its Starlink satellite internet service to deliver cloud computing services to business customers.
Under the partnership, SpaceX will place its Starlink ground stations within Google data center properties, which can help the service support businesses requiring cloud-based applications.
Starlink is in the process of launching its satellite broadband internet service, which can reach customers without ground-based connections and is one of several space-based systems.
"Combining Starlink's high-speed, low-latency broadband with Google's infrastructure and capabilities provides global organizations with the secure and fast connection that modern organizations expect," said SpaceX president and chief operating officer Gwynne Shotwell.
"We are proud to work with Google to deliver this access to businesses, public sector organizations, and many other groups operating around the world."
Urs Hoelzle, senior vice president at Google Cloud, said the tie-up would help ensure "that organizations with distributed footprints have seamless, secure, and fast access to the critical applications and services they need to keep their teams up and running."
This new capability for enterprise customers is expected to be available in the second half of 2021, the companies said in a joint statement.
SpaceX is seeking regulatory approval for broadband service for both consumers and businesses around the world from thousands of satellites.
Phy.Org
|
|